
Here at Novaworks,
information security is a high priority. After the of announcement of CVE-2014-3566, we immediately patched our servers to no longer support SSL 3.0. Other major services such as Google, LinkedIn and CloudFlare have already disabled
SSL 3.0 or are planning to do so in the upcoming months. We encourage our users to update their browsers and proxies to support
TLS 1.0 or later.
What do I need to know?
There is a vulnerability in the way the SSL 3.0 protocol was designed that may allow a third-party to decrypt traffic between your computer and a secure server. This
security vulnerability is a “man-in-the-middle” exploit that does require the malicious user to be on the same network as your computer (such as a shared wireless network). Furthermore, this exploit is a general problem with the
SSL 3.0 protocol – not a specific implementation of the protocol. This means it affects all devices that use the protocol, from computers to tablets to phones, regardless of operating system or manufacturer.
What do I need to do?
Make sure that TLS 1.0 or later is checked in your computer’s Internet Options. These options are accessible through the Tools menu in Internet Explorer or from the Control Panel. IT professionals can use a group policy to enforce these changes for all computers in your organization.
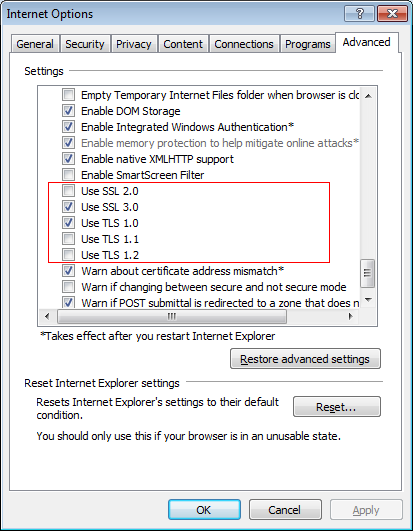
Please note that depending on the version of Internet Explorer that is installed on your computer, this dialog may not have TLS 1.1 and/or TLS 1.2. For users running Windows XP, make sure Service Pack 3 and Internet Explorer 7 or later is installed. For Windows Server 2003, make sure Service Pack 2 and Internet Explorer 8 is installed (available through Windows Update only).
Are there any other ramifications to these changes?
If TLS 1.0 was disabled on your computer, you may want to find out why. In 2011, a vulnerability known as
BEAST was found in some of the encryption methods used in TLS 1.0. At the time, the advised action was to downgrade to SSL 3.0 and use different encryption methods, but now it is better to disable the problematic ciphers rather than the entire protocol. Many vendors have already released patches to prevent the problem. See the references below for information on selecting available ciphers in Windows.
TLS 1.1 and 1.2 are disabled by default on Windows 7. This is because many servers did not support the protocols at the time that Windows 7 was released. Additionally, renegotiating with servers can take extra time and SSL 3.0 was considered secure enough that additional protocols did not need to be employed.
If you are using SSL 3.0 because you do not want to use TLS 1.0 and TLS 1.1 and TLS 1.2 are not available, consider updating your software. TLS 1.0 came out almost 20 years ago. There are many advantages to upgrading as opposed to using older technology.
Keep in mind that you do not need to disable support for SSL 3.0, but it is recommended that you do so because it is the reason for the vulnerability. As of 2014, only 2% of web servers in the world support only SSL 3.0. Disabling SSL 3.0 will prevent you from securely contacting those specific web servers. If you frequently communicate with such a server, you may need to continue to have SSL 3.0 enabled until such a time that those servers upgrade their protocols.
What if my corporation uses a proxy?
Make sure your IT department knows about this vulnerability. They will need to update the proxy software in order to remedy the situation.
Why is correcting this vulnerability so important?
Information security and
cybersecurity is extremely important, particularly when working with sensitive documents, so it’s important to keep abreast of
internet security vulnerabilities and make corrections as appropriate. While communicating with our servers does not necessarily compromise the security of your documents, as the most common communication between
GoFiler and our server is to register a key or download a software update, this vulnerability did affect such activities as using the Bug Report feature or sending secure e-mails, so you can understand why we immediately patched our servers.
Keeping your data secure is a top priority at Novaworks, even if patching our servers could cause a brief inconvenience to some of our customers. If you find that you are no longer able to register your software key or open your
filing software, it is likely because you have SSL 3.0 enabled without having TLS 1.0 or better also enabled. Please follow the advice posted above as soon as possible.
Further Reading:
http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-3566
https://technet.microsoft.com/en-us/library/security/3009008.aspx
http://support2.microsoft.com/default.aspx?scid=kb;EN-US;245030
http://googleonlinesecurity.blogspot.co.uk/2014/10/this-poodle-bites-exploiting-ssl-30.html
http://news.netcraft.com/archives/2014/10/15/googles-poodle-affects-oodles.html